Most people never need to think about advanced VPN settings.
And that’s fine.
But if you’ve been using a VPN for a while, certain questions start appearing on their own. Why does speed change so much between servers? Why do some apps behave strangely only when the VPN is on? Why does everything work perfectly at home but fall apart on hotel Wi-Fi?
These aren’t beginner questions anymore. There are signs that you’ve moved past “turn it on and forget it” and into understanding how VPNs behave in real environments.
Advanced VPN usage isn’t about becoming paranoid or locking everything down. It’s about knowing where the edges are and choosing how close you want to stand to them.
If you haven’t already, it helps to be clear on what VPNs do and don’t protect in the first place. Without that grounding, advanced settings tend to cause more confusion than clarity.
Why “Advanced” Doesn’t Mean “More Secure”
One of the quiet myths around VPNs is that more settings automatically mean better privacy.
In reality, every advanced option introduces a trade-off. More control often means more points of failure. What feels empowering in a settings menu can quickly turn into broken apps, leaking connections, or false confidence.
Advanced VPN usage is less about maximising protection and more about aligning behaviour with intent.
That mindset matters far more than any toggle.
Protocol Choice: Why It Sometimes Matters (And Often Doesn’t)
At some point, most advanced users notice protocol options: WireGuard, OpenVPN, IKEv2, etc.
At a high level, these define how your device creates and maintains the encrypted tunnel. In everyday use, WireGuard tends to feel faster and more stable, especially on modern devices. OpenVPN trades a bit of speed for flexibility and maturity. IKEv2 handles network switching gracefully, which is why it behaves well on mobile connections.

But here’s the part that rarely gets said plainly: for most people, the default protocol is already the right one.
Manually switching protocols only makes sense when you’re solving a specific problem—unstable connections, blocked networks, or compatibility issues. Treat protocol changes as a troubleshooting step, not an upgrade.
Split Tunnelling: Convenience With Sharp Edges
Split tunnelling lets some apps use the VPN while others bypass it.
On paper, it sounds perfect. Your browser stays protected while streaming apps work normally. Your banking app avoids extra verification while everything else stays encrypted.
In practice, split tunnelling requires restraint. Once you start dividing traffic, you’re responsible for remembering which apps are protected and which aren’t. That’s fine if you’re intentional. It’s risky if you forget—or assume more is protected than actually is.
Split tunnelling works best when used sparingly and revisited occasionally. If you can’t remember how you configured it last month, it’s probably doing more harm than good.
DNS Leaks: The Issue People Worry About More Than Necessary
DNS leaks are often described as catastrophic privacy failures. In reality, they’re usually mundane.
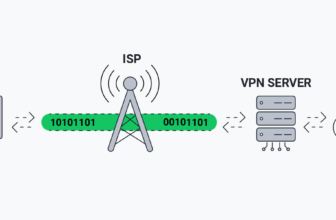
DNS requests are how your device asks where websites live. A well-configured VPN routes these requests through the tunnel. A poorly configured one might not.
Most reputable VPN apps handle this correctly by default. Problems tend to appear when users mix custom DNS settings, third-party apps, or aggressive split tunnelling.
If you haven’t manually changed DNS settings, you’re probably fine. If you have, it’s worth double-checking but not obsessing. Advanced usage is about awareness, not constant vigilance.
Threat Models: The Question Advanced Users Eventually Ask
At some point, advanced users stop asking, “Is this secure?” They start asking, “Secure from whom?” This is where threat models come in.
A VPN is excellent at protecting against casual network snooping and untrusted infrastructure. It’s not designed to protect against targeted surveillance, compromised devices, or identity-based tracking.
If your concerns involve activists, journalists, or high-risk environments, a VPN is only one small part of a much larger conversation. If your concerns are everyday privacy and safer connections, a VPN may already be doing exactly what you need.
Knowing which category you fall into prevents both under- and over-engineering.
Why Advanced Setups Sometimes Feel Fragile
As VPN usage becomes more complex, stability often decreases.
Multiple devices. Custom protocols. Split tunnelling. Kill switchesare layered on top of unstable networks. None of these is inherently bad, but together, they create systems that are easier to disrupt.
This is why advanced users should periodically simplify. If something breaks and you can’t immediately explain why, that’s a sign the setup has drifted beyond usefulness. Rolling back to defaults isn’t a failure. It’s maintenance.
How This Connects Back to Beginner VPN Use
Advanced usage doesn’t replace beginner habits. It builds on them.
The same principles still apply: use VPNs deliberately, turn them off when they cause friction, and don’t expect them to solve problems they weren’t designed to handle.
If you’re guiding someone new to VPNs, it’s often better to point them to a beginner-focused explanation before introducing advanced features. Complexity makes sense only after the fundamentals are clear.
Where the Core VPN Guide Still Matters
Even for advanced users, it’s easy to drift into assumptions.
Revisiting the core explanation of what VPNs protect—and what they don’t—helps reset expectations. Advanced settings don’t change the fundamental limits of VPNs. They just change how you interact with those limits.
That perspective keeps advanced usage grounded instead of being obsessive.
A Calm Way to Think About Advanced VPNs
Advanced VPN usage isn’t about squeezing out maximum privacy at all costs. It’s about understanding trade-offs well enough to choose them consciously.
Sometimes that means custom configurations. Sometimes it means going back to defaults. Both can be correct, depending on context.
When advanced VPN usage feels calm rather than tense, you’re probably doing it right.